Test Driving CIFv5
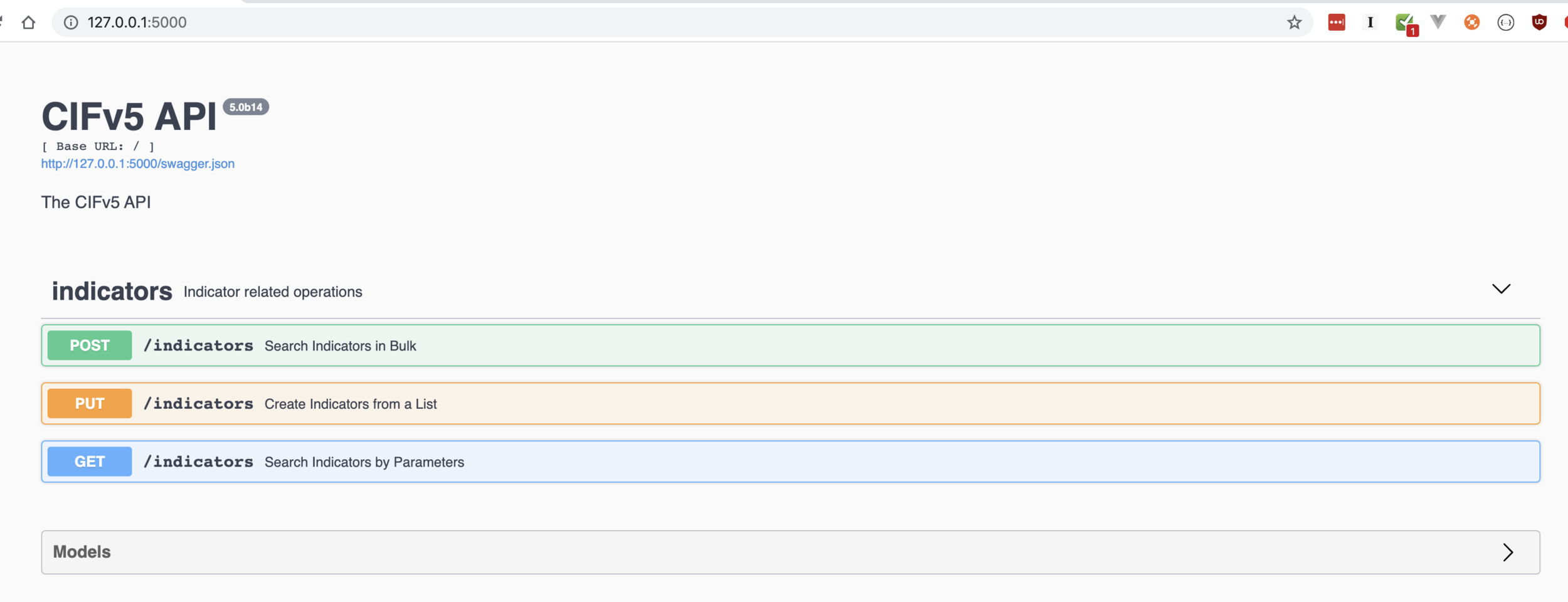
Solve problems by writing doc first.
Solve problems by writing doc first.
The fastest way to threat intel is …
How to Brick your laptop- searching for ASN Information…
Not everyone can be Chuck Norris.
I remember my first security technology spending spree… it crashed the housing market.
If you haven’t checked out THE eCrime conference, you’re…
Being happy- is in having the vision to build a rocket ship, executed by building better and better skateboards.





